WikiLeaks is back with yet another batch of Vault 7 related documents
detailing the CIA’s (Central Intelligence Agency) hacking tools and
programs targeting unsuspected users worldwide for large-scale cyber
espionage.
The latest leak exposes “Highrise,” a malware disguised as an app called TideCheck employed by CIA to target Android devices running on versions 4.0 and 4.3 – WikiLeaks has described the app as “CIA Android phone SMS proxy ‘HighRise’ which masquerades as ‘TideCheck’ to form a covert messaging network.”
The TideCheck app does not work like conventional apps since the attacker needs to have a physical access to the targeted device. Therefore, it can only be downloaded, installed and activated manually.

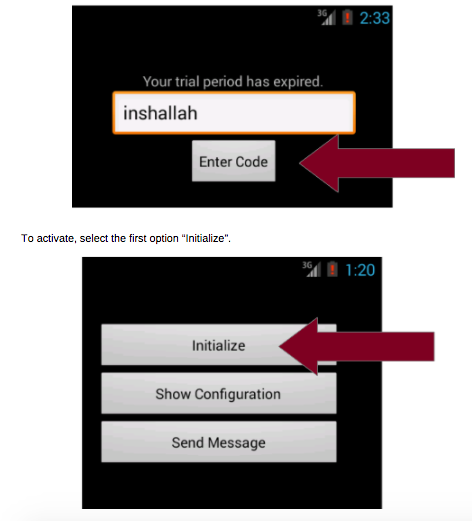
However, targeted users can also be tricked into installing the app, but it requires users to open the app, enter the password which is “inshallah,” an Arabic word meaning “if Allah wills it” or “God Willing.” Once installed, the app will run stealthily upon reboot.
Upon detailed analysis of the Highrise’s user manual leaked by WikiLeaks, it can be seen that the app documents highlight HighRise v2.0 from 16, 2013. Since last four years, Google has issued numerous updates for Android devices.
Therefore, the only way of concluding the app’s current status is based on whether or not the CIA has also updated the app based on the security updates issued by Google to counter increasing malware attacks against Android devices.
OutlawCountry and Elsa: Malware targeting Linux devices and tracking user geo-location
Brutal Kangaroo: CIA hacking tools for hacking air-gapped PCs
Cherry Blossom: CherryBlossom & CherryBomb: Infecting WiFi routers for years
Pandemic: A malware hacking Windows devices
AfterMidnight and Assassin: CIA remote control & subversion malware hacking Windows
Dark Matter: CIA hacking tool infiltrating iPhones and MacBooks
Athena: A malware targeting Windows operating system
Archimedes: A program helping CIA to hack computers inside a Local Area Network
HIVE: CIA implants to transfer exfiltrated information from target machines
Grasshopper: A malware payloads for Microsoft Windows operating systems
Marble: A framework used to hamper antivirus companies from attributing malware
Dark Matter: A CIA project that infects Apple Mac firmware
The latest leak exposes “Highrise,” a malware disguised as an app called TideCheck employed by CIA to target Android devices running on versions 4.0 and 4.3 – WikiLeaks has described the app as “CIA Android phone SMS proxy ‘HighRise’ which masquerades as ‘TideCheck’ to form a covert messaging network.”
The TideCheck app does not work like conventional apps since the attacker needs to have a physical access to the targeted device. Therefore, it can only be downloaded, installed and activated manually.

However, targeted users can also be tricked into installing the app, but it requires users to open the app, enter the password which is “inshallah,” an Arabic word meaning “if Allah wills it” or “God Willing.” Once installed, the app will run stealthily upon reboot.

“Highrise
provides a redirector function for SMS messaging that could be used by a
number of IOC tools that use SMS messages for communication between
implants and listening posts. HighRise acts as an SMS proxy that
provides greater separation between devices in the field (“targets”) and
the listening post (LP) by proxying “incoming” and “outgoing” SMS
messages to an Internet LP. Highrise provides a communications channel
between the HighRise field operator and the LP with a TLS/SSL secured
internet communication.”
It
is unclear why the password was chosen as “Inshallah” which is a term
Muslims around the world freely use. One reason could be that the app
was developed to target Arabs or Muslims in general.Upon detailed analysis of the Highrise’s user manual leaked by WikiLeaks, it can be seen that the app documents highlight HighRise v2.0 from 16, 2013. Since last four years, Google has issued numerous updates for Android devices.
Therefore, the only way of concluding the app’s current status is based on whether or not the CIA has also updated the app based on the security updates issued by Google to counter increasing malware attacks against Android devices.
Vault 7 document previously leaked documents by WikiLeaks
BothanSpy and Gyrfalcon: Steals SSH credentials from Linux & Windows devicesOutlawCountry and Elsa: Malware targeting Linux devices and tracking user geo-location
Brutal Kangaroo: CIA hacking tools for hacking air-gapped PCs
Cherry Blossom: CherryBlossom & CherryBomb: Infecting WiFi routers for years
Pandemic: A malware hacking Windows devices
AfterMidnight and Assassin: CIA remote control & subversion malware hacking Windows
Dark Matter: CIA hacking tool infiltrating iPhones and MacBooks
Athena: A malware targeting Windows operating system
Archimedes: A program helping CIA to hack computers inside a Local Area Network
HIVE: CIA implants to transfer exfiltrated information from target machines
Grasshopper: A malware payloads for Microsoft Windows operating systems
Marble: A framework used to hamper antivirus companies from attributing malware
Dark Matter: A CIA project that infects Apple Mac firmware

