I used to be where you are – most likely a technical person not fully enjoying what you do at your day job and wanting to make the move to a job that you would actually enjoy in the security field.
For me specifically, that was conducting vulnerability assessments, penetration testing, hacking, auditing or anything in the IT Security field.
On the About Me page I described a little bit about how I got where I am. Now I’m going to share with you exactly what I would do if I could do it all over again, but first I’m going to answer a few popular questions about the industry.
Is a Computer Science degree necessary to be a pentester?
So you want to learn how to hack and think you need a degree. If you have the time and the money to pursue a degree in computer science, by all means take the opportunity and pursue it. While it is not necessary to have this degree, it would be one of the optimal paths to take under perfect conditions to get your foot in the door at an entry-level position.
You might be pursuing or have other technical degrees already that could substitute nicely. I personally had a Computer Information Systems (CIS) degree when I set out on my journey.
To go a bit further I decided to get a Masters in Information Security and Assurance, but this isn’t necessary for everyone. If you were coming from a non-technical field though, a switch to a more technical masters program could be just the path for you.
Don’t let the BS and MS degree talk deter you though if getting one isn’t an option. Technical degrees are always an option as well.
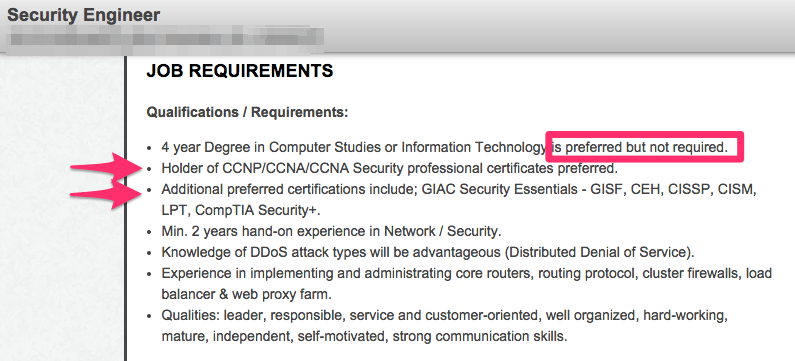
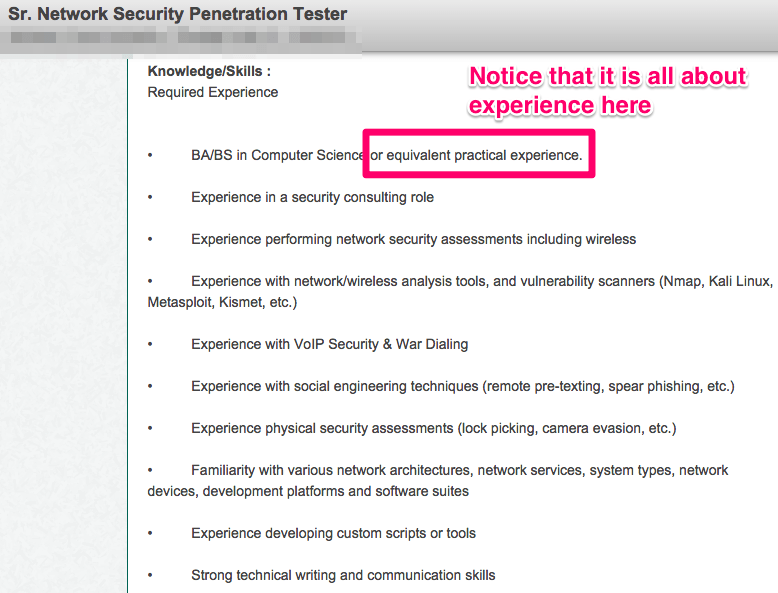
While you will always find that companies are looking for a degree, if you have the right experience and certifications it surely wouldn’t hold you back at all.
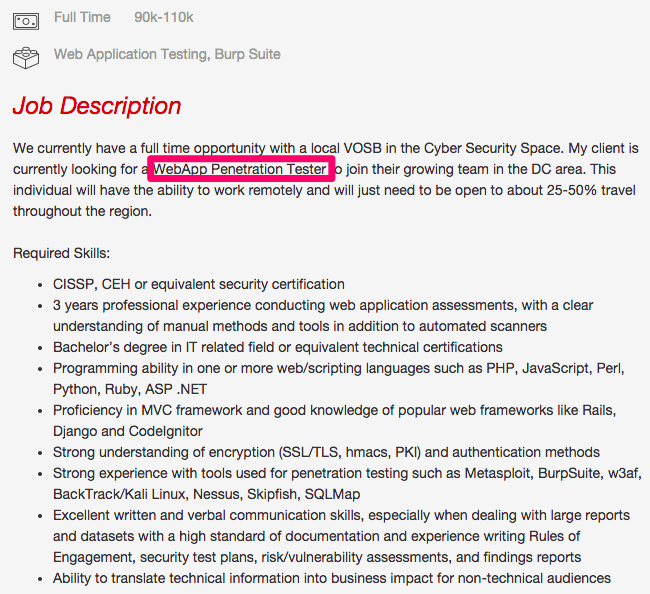
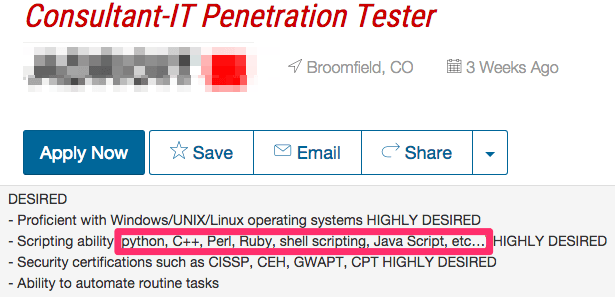
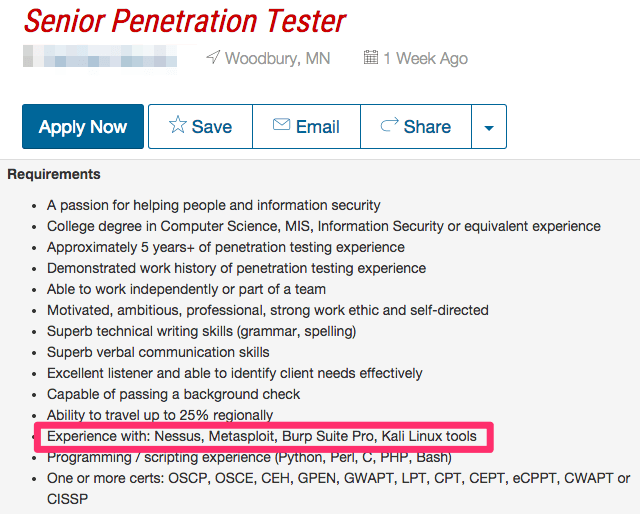
Let’s take a look at two sample information security job postings:
Does where I go to school matter?
In my opinion, it doesn’t matter where you obtain your degree. You would just use this as a stepping stool to gain some fundamentals (Join our list to start getting those fundamentals now) and get your foot in the door so that potential clients feel comfortable with you. Sometimes they will actually ask for your resume and a degree looks good on there.
Surprisingly, Vo Tech and Community Colleges often have programs that are just as good as the more prestigious schools. Many times, you can get just as good an education for half the cost and in half the time.
What matters most though is the amount and type of experience that you will be able to gain along the way as was hinted in the graph above.
You should note that even the most expensive college or university does not necessarily have the best educational programs for this particular field. At this point in time this field is in its infancy, which also means that this is actually a great time to get into the field before it becomes crowded.
Most computer science programs available today place the majority of emphasis on programming, although I foresee them moving heavily in the cyber security direction over time, including Pentesting.
Some schools now even have cyber security degrees, so if you know for sure that this is the area you want to be in then I would take a hard look at that.
That large programming aspect of the computer science programs will also be very beneficial to you later without a doubt.
Which certifications should I have?
Certain certifications will be indispensable when it comes to getting your foot in the door, especially if you pick the right ones.
It may seem like putting the cart before the horse by getting one of these before you get the experience and it is, but having one will give you a leg up over another candidate who doesn’t have one.
It is also very doable to get one in a relatively short period of time, unlike a degree.
This is why if you already have a Bachelor’s degree I wouldn’t recommend going back to get a computer science degree, but instead going after some of the sought after certifications such as: SANS – GPEN, GWPT, GSEC, GAWN; Offensive Security – OSCP, OSWP, OSCE, OSEE; EC-Council – C|EH, ECSA, ECSA L|PT.
There are also others that you can find with a simple Google search or by looking at job postings online.
While it’s not necessary that you obtain all of these certifications, you will want to be able to prove that you have the required experience to perform the job and some of these certifications will help you do just that.
You’ll also want to consider some networking certifications such as Network to start, or even better the CCNA. You will commonly see the CCNA certification listed on pentesting job requirements.
These certifications will go a long way towards helping you obtain a penetration-testing job and can be just the thing that propels you ahead of another candidate vying for the same job.
These certifications will go a long way towards helping you obtain a penetration-testing job and can be just the thing that propels you ahead of another candidate vying for the same job.
What experience should I have?
Don’t make the mistake of getting a ton of certifications and forgetting that above all else experience is king. You may make it to the interview, but when the interviewer starts asking about experience, things could start to go downhill fast for you.
While you may not need experience for some entry-level positions, it is critical to get some if you expect to succeed and for a leg up on other entry-level applicants.
A solid understanding of networks is also critical for you. You don’t have to be an expert and can learn along the way, but you need to have a somewhat solid overview of how they work.
I was given an IP address in an interview some years back and asked what the broadcast address was. You need to be able to answer simple questions like this, so if you can’t you probably need more training in this area.
Building a home lab network environment is critical for a penetration tester and will allow you to get a better understanding of penetration testing, hacking, networking and help you meet the experience requirement you will need.
You will also want to become well versed in working and testing Web Applications and Cloud technologies such as SaaS. Web Application testing is very hot right now and you might have already noticed this while looking at some of the new pentesting positions available.
Building a home lab network environment is critical for a penetration tester and will allow you to get a better understanding of penetration testing, hacking, networking and help you meet the experience requirement you will need.
You will also want to become well versed in working and testing Web Applications and Cloud technologies such as SaaS. Web Application testing is very hot right now and you might have already noticed this while looking at some of the new pentesting positions available.
Because everything is moving out to the Cloud, companies are actively looking for people with the specific skills to test these applications and being advanced in this area can help you stand out from the competition.
Another great way to get experience is by reaching out to people in the industry already and working for them for free in your spare time.
This will give you documentable work experience beyond your own home lab and you may even get an opportunity to work with that company as well.
What skills do I need and is a networking background required?
You must know the fundamentals. That being said, I part ways with some in the industry here as some believe you need many years of experience as a network administrator or security engineer etc. first before moving on to pentesting. I actually believe that this isn’t a requirement and think you can learn both concurrently depending on your skill level and willingness to learn. They complement each other.
If you are dedicated you can read both types of books, take both types of classes and experiment with both sides of the same coin. Learning how to pentest doesn’t prevent you from concurrently learning how networks work.
However, learning how to pentest and hack without learning how networks work is never going to happen for you, so go get those fundamentals down.
Do I need to know how to code?
While you don’t need to be an advanced level coder to penetration test, it would be very wise to start learning some basic scripting in order for you to hack together some tools that you need.
The key here is to get some basic things to work, not to build out some huge application. You might have specific needs according to a penetration test that you are conducting and may need to tweak an already existing application or build your own.
You may commonly run into a Metasploit module that doesn’t meet your needs at the moment and you may need to either modify one or write it from scratch in ruby.
Most penetration testers can code in many languages because after you learn one language it isn’t difficult to branch out to others.
In my opinion you should focus on learning Ruby or Python because most of the code and job prerequisites you will come across will be written in one of the two. Both are often used in the penetration world and are the de facto standards. Build it once and then use it forever.
As you gain experience, you can start to branch out to some other languages as well. This knowledge base will make you more attractive in interviews and make you a much better pentester.
Start by watching some YouTube videos and then go and modify or try to recreate those applications on your own.
What is the best way to find a job?
The best way to find a job is to first look at your current employer to see if you can tweak your position or move to another in the company. The next best route would be to intern somewhere if you can.
If you can’t do it those ways you can always start your search by going to job searching sites such as the Federal Government (USAJobs.gov), CareerBuilder, Monster.com, Indeed.com and Dice.com.
Be on the lookout for titles such as Information Security Analyst, Information Security Auditor, Information Security Engineer, IT Security Consultant, and of course Penetration Tester. Of course you can search for common keywords such as Kali, Nessus, Wireshark, Metasploit, Burp Suite and nmap.
These will always vary and change over time, but you should be able to come up with a few different combinations and find some openings without issue.
Companies are looking for people who are willing to learn and do what it takes to get the job done.
If you don’t have a specific skill but are willing to pick it up along the way then it doesn’t matter at all. Presenting yourself to the company that way will significantly increase your chances of obtaining the position.
When interviewing for my first position, I personally had some good education but the direct experience wasn’t there. However, the company decided to take a chance on me based on my willingness to learn and get the certifications I obtained.
How much money do pentesters make?
As with any job this depends on many variables, but I’ve included a general range for you here:
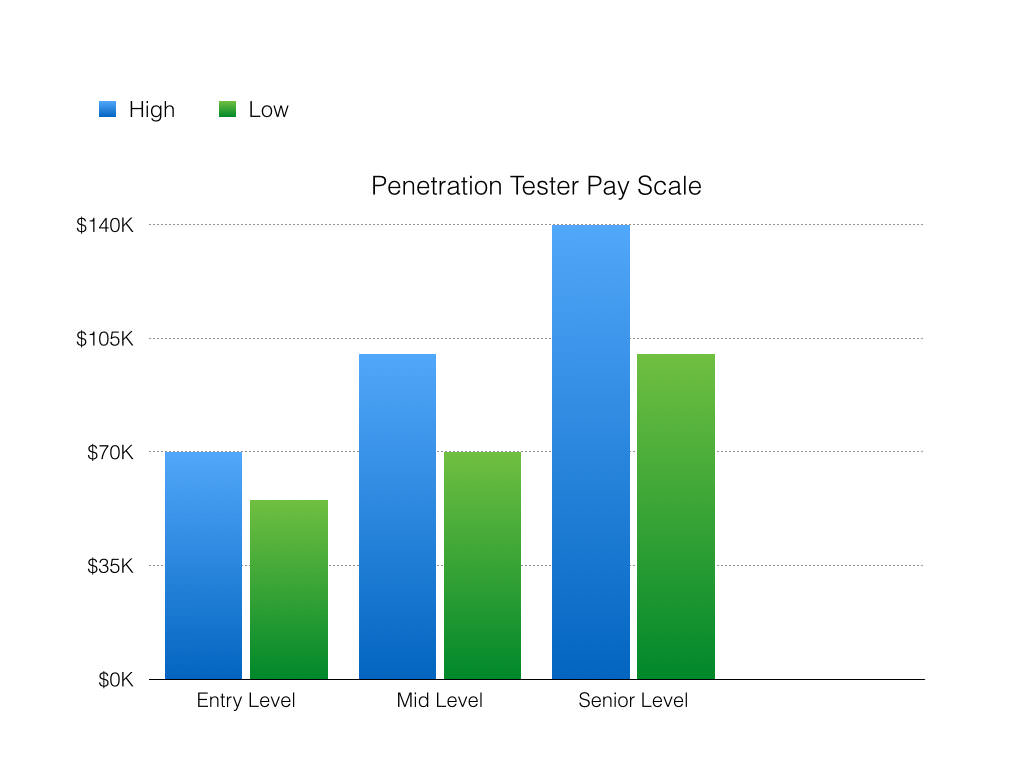
It isn’t uncommon for entry-level positions to be between 55k-70k, mid-level to be between 70k-100k and senior level to be between 100k-140k.
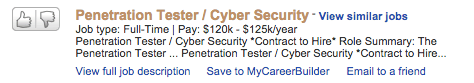
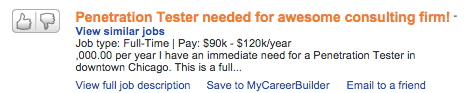
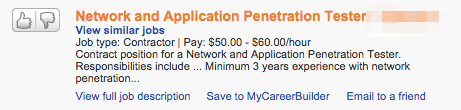
If I had to do it all over again this is what I would do:
Step #1: I would evaluate my day job
I would evaluate my current position at my job and see if there was any way that I could gain some experience right where I am.
If there were a way to focus on some networking fundamentals or administration fundamentals I would start there. Many of you are already in technical positions, so take a look around, start reading more networking/hacking/pentesting books and see how you can apply it all to your current position.
Step #2: Set up my home lab
At the same time as I’m evaluating my day job, I would be setting up a virtual lab at home (download the step-by-step ebook) to start studying how everything works. To see how I would do that you can take a look at this page here.
In the process I would start looking at some basic videos on networking, hacking, pen testing, Ruby and Python. I’d utilize SecurityTube (http://www.securitytube.net/) and YouTube for this. As my skills got better and my knowledge base expanded I would also expand on this home lab network as well so I could run more tests.
Step #3: I would get web application testing down
After I got pretty confident on how things work in my own home lab I would be looking for other web applications and networks to learn on. OWASP, the Open Web Application Security Project, has an awesome complete list of vulnerable websites that you can learn on. You can find that list here:
Step #4: I would become the go-to security guy
After I became more confident I would then proceed to utilize what I’ve been learning at my current position with permission.
After I got some basic fundamentals down or if I already had the fundamentals down I would let my manager know that I would be happy to evaluate the current security situation in my own time if he/she would allow me.
I would try to position myself as the security guy on the team and make it my responsibility to learn all that I could. This would get my resume looking pretty good when it comes to experience and allow me to get even more much needed experience.
Step #5: Get a mentor
If it weren’t possible to get some experience at my current job, I would start by doing a cursory search of LinkedIn looking for people who are current penetration testers, security engineers or analysts, and reach out to them to do unpaid internships. I would let them know that I would help out in any way I could.
The great thing about LinkedIn is that the people that you find in your search will be 1st and 2nd connections to you, which is great as it will make it easier to connect to them and they are most likely in your area as well.
Some other searches to try:
IT Security Consultant
Information Security Engineer
Information Security Analyst
Information Security Auditor
Information Security Engineer
Information Security Analyst
Information Security Auditor
This internship could help you get your foot in the door at the company or at the very least you will gain experience that you can now put on your resume.
Step #6: Get certified in something
I would look at getting a certification to supplement the experience that I am getting. I would focus on ONE sought after certification that I am able to get based on my current experience and the experience requirements of the certification.
I would spend the rest of my time trying to gain that valuable experience that I need as nothing is going to replace it.
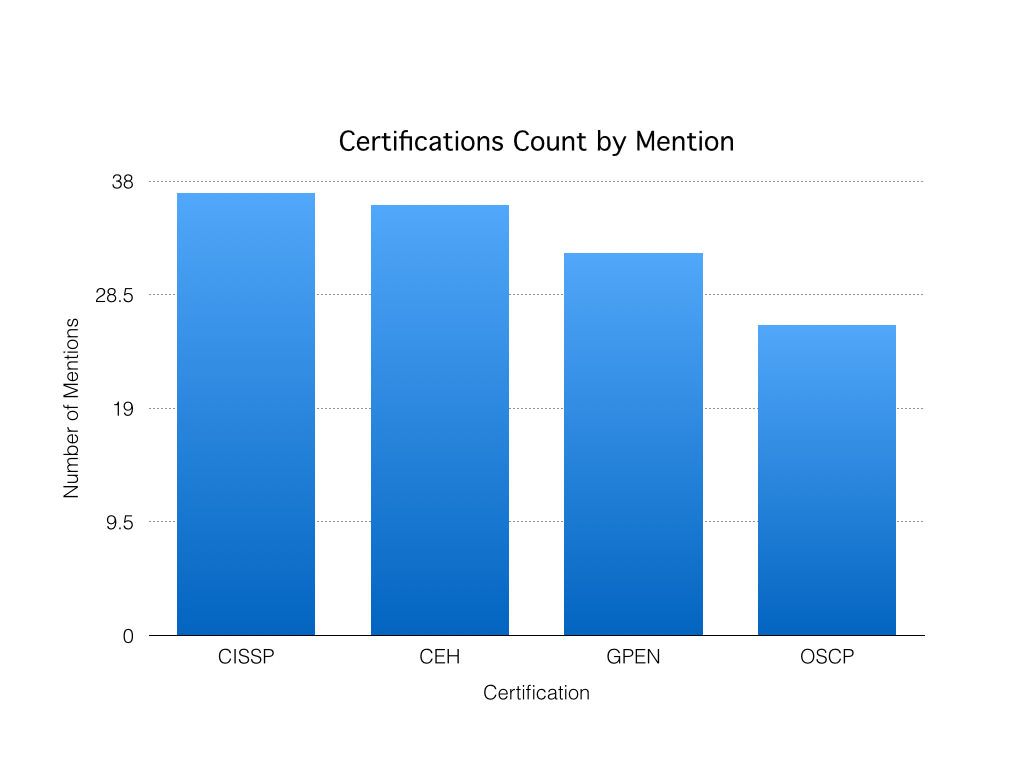
The four certifications that I would choose from at the beginning are the OSCP, CISSP, CEH or GPEN. This is completely my opinion and you probably have a different list.
Most penetration testers will tell you that a OSCP, CISSP, CEH OR GPEN certification will not make you a penetration tester, that only experience will, and that is absolutely true.
Only your experience and skill will make you a penetration tester. However, most wouldn’t deny that companies actively make their interview/hiring decisions based on certifications. The four certifications were chosen based on my quick research online of job postings.
To see what certifications companies were looking for, I searched for penetration testing or info security jobs and looked at the first 50 that I came by.
Of course this isn’t very scientific – I was only looking for the top 4 mentioned certifications and there should be a larger sample size – but I went with 50. The results actually surprised me but here they are:
If you do this test yourself you will get different results because of a different sample, but you will most likely see fairly similar results.
I did not expect the CISSP to be mentioned as often as it was for penetration testing positions, but it just goes to show how popular that certification is in the eyes of employers no matter what spectrum of IT Security you land on.
Some of you may argue that the OSCP certification is the best of these to get and I wouldn’t argue with you. Again, this isn’t scientific and I don’t have an opinion at all, but this should give you an idea of what companies are looking for.
Of course there were other certification mentions such as the CCNA, but I decided to go with the top four mentioned here. I encourage you to take a look at these jobs and see what they are looking for as well.
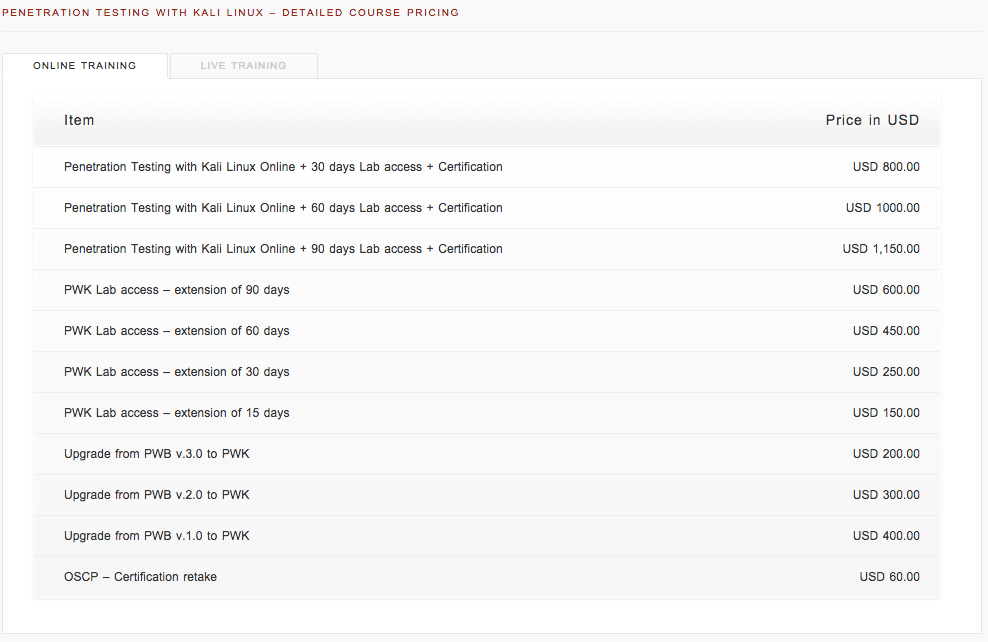
Now, let’s take a look at what the hit will be like for your wallet.
OSCP
CISSP
CEH
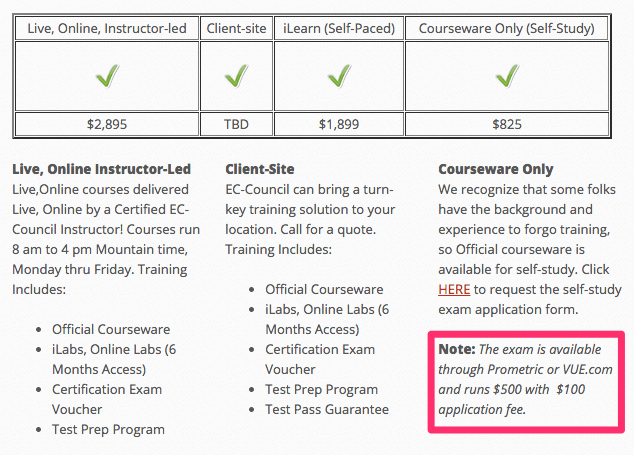
GPEN

The objective for us right now is to get to a point where we can get that experience, and these certifications are still some of the more popular certifications that a HR Manager at some company will be looking for.
We can educate ourselves on our own and we will, but other than our own hard work nothing will get you where you want to be quicker than being forced to learn at your day job.
Lets take a look at some experience requirements for these certs:
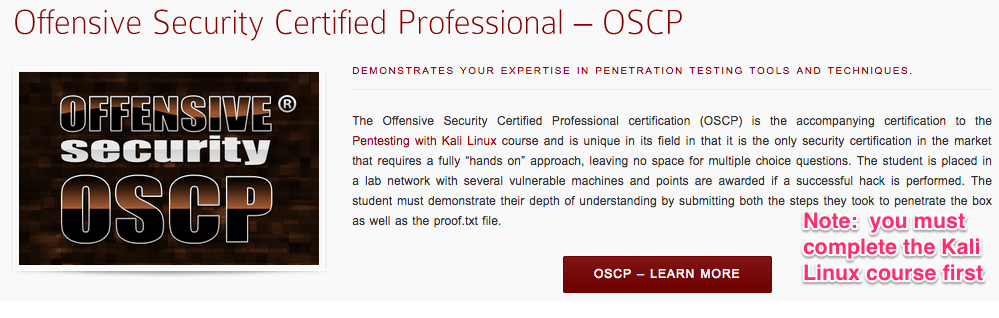
OSCP
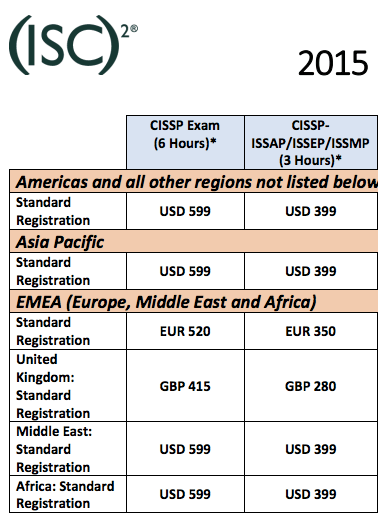
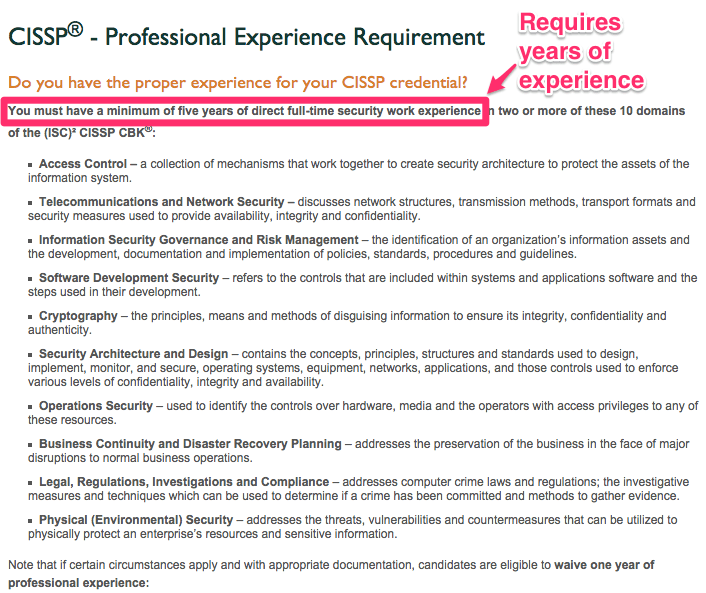
CISSP
CEH

GPEN
We can see that the CISSP certification requirement is heavy, so if you don’t meet the experience requirements I would come back to it at a later date. I actually did that myself. I started with a couple others such as C|EH before later getting the CISSP. Another CISSP option is by becoming an associate and getting the experience along the way until you reach the requirements for the full certification.
After getting some certifications, I considered getting even more until I realized that it really just doesn’t matter all that much. It is just my personal opinion that certifications should be used as a tool to get you where you need to be, but after you are there, experience alone is king.
It would be awesome if you got all of these certifications, but nothing beats having the right experience and that is now where I focus most of my time.
It is important however that you get a few certifications just to demonstrate your competency both from a job standpoint and client standpoint. At the end of the day though, clients and employers will primarily be looking for you to have relevant past experience of conducting these tests in the field.
Certifications are mainly good to get your foot in the door at a security firm so just pick one and run with it!
Step #7: I would Capture The Flag and take challenges
At Hack This Site (https://www.hackthissite.org) there are many free challenges that you can take. It doesn’t get much better than that. I would start basic and work my way up from there. After I did a few of these I would move on to Capturing The Flag events.
At CTF Time (https://ctftime.org/event/list/) there are a ton of online and offline Capture The Flag events that you can be a part of.
When I felt my skills were up to the task I would try my best to be a part of a team and get involved in some of these events. For me this would be both a good time and give me the ability to practice in a scenario that is closer to “real-world”.
Step #8: Look for entry-level positions
At the beginning I would be looking to get my foot in the door, understanding that I may take a hit on pay for a bit while I gain the much needed experience so that I can transition to another field.
If you truly see this as your passion you should be willing to take less in order to make a move into something you love and the money will follow. “Choose a job you love, and you will never have to work a day in your life.” – unknown
People will always need and be looking for pentesters, so after you have gotten your experience, certifications etc. the employers will start looking for you rather than the other way around.
You will always feel as though you need more certifications, more experience and someone to knight you. You don’t; just go get started and get into the industry.
I’ve put together a package of things to help you execute on these steps:
- Ebook to help you set up your own pentesting lab.
- Ebook to help you customize that pentesting lab.
- Sample LinkedIn email I would send to start connecting and get experience
- How to get through the interview process
- I created a decision tree to show you the most optimal route for you to take to become a pentester.