
ESET, the Slovakian anti-virus software firm and Dragos, the US-based infrastructure security company recently discovered an industrial malware dubbed as “Crash Override” or “Industroyer” to have hacked into the Ukraine’s power grid in December 2015 and has caused a power outage for hours.
A more advanced form
The malware which caused the power outage in December 2015 was found by the security firms only recently and has been named Crash Override, otherwise known as “Industroyer.” The one found now, however, is considered to be more advanced and is believed to have the potential to cause a major power supply outage.The security firms stated that the malware which caused the power outage in 2015 was perhaps just a trial run to see whether the technique works on not. Dragos also stated that (PDF) while the previous malware only caused an outage for some hours, Crash Override can do so for days.
Command over industrial processes
Researchers fear that this latest version is highly potent regarding its capability to understand industrial processes and manipulate them as the attackers have directed it. Essentially, when it comes to power grids, researchers say that the malware can communicate between relay points and hence control the system altogether.The industrial communication protocols of the virus are much more sophisticated and can therefore not only be applied to hack into power systems but can also be deployed in other major services such as transportation, water supply, and other similar nation-wide systems.
What is more frightening is the fact that the malware was designed to affect systems that were created without any security protocols. This means that attackers today, need not search for any glitches or flaws as the entire infrastructure does not have any immune system in the first place.
This is combined with the fact that the malware works as a digital switch, meaning the damage that can be caused by the malware can be much more far-reaching as it can simply switch on or off the power supply anytime.
How was the malware discovered?
According to reports, the researchers at Dragos were given cryptographic hashes of the malware from their partners ESET. It was during the investigation of these that Dragos stumbled over the mighty Crash Override.Dragos got involved into the investigation as it believed that the malware could be used against the U.S. The firm stated that the virus only needed a little bit of tweaking to hack into U.S systems and those of wider Europe.
According to ESET’s findings and blog post:
“Industroyer is a particularly dangerous threat since
it is capable of controlling electricity substation switches and
circuit breakers directly. To do so, it uses industrial communication
protocols used worldwide in power-supply infrastructure, transportation
control systems, and other critical infrastructure systems (such as
water and gas).
These switches and circuit breakers are digital equivalents of analog
switches; technically they can be engineered to perform various
functions. Thus, the potential impact may range from simply turning off
power distribution, cascading failures and more serious damage to
equipment. The severity may also vary from one substation to another, as
well. Needless to say, disruption of such systems can directly or
indirectly affect the functioning of vital services.
Industroyer’s
dangerousness lies in the fact that it uses protocols in the way they
were designed to be used. The problem is that these protocols were
designed decades ago, and back then industrial systems were meant to be
isolated from the outside world. Thus, their communication protocols
were not designed with security in mind. That means that the attackers
didn’t need to be looking for protocol vulnerabilities; all they needed
was to teach the malware “to speak” those protocols.”
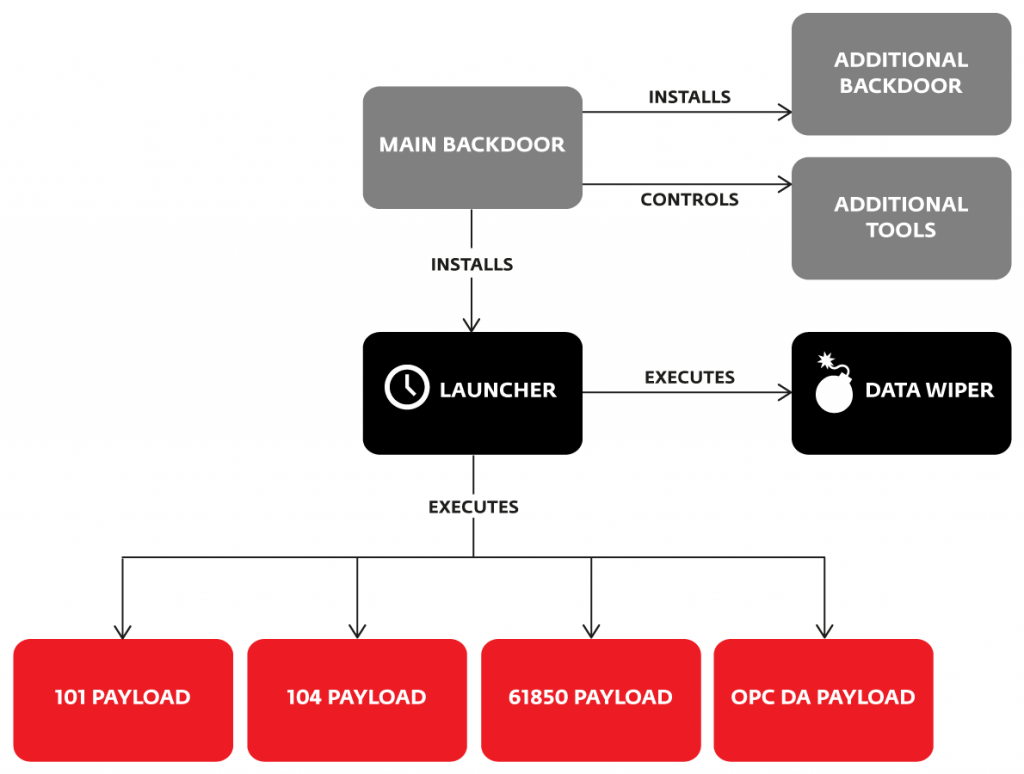
Malware with Command-and-Control Centers imply additional danger
Researchers at Dragos stated that although the malware is quite powerful in that it can fluently communicate with the industrial process, it is, however, even more, dangerous as it deploys conventional malware attacking methods.That is, the malware has the ability to distort information and as such, make troubleshooting systems all the more difficult. Also, the malware can use various methods to attack as was evidenced by the fact that it hacked into a control system manufactured by Siemens by exploiting a certain vulnerability that existed therein.
Nevertheless, the ubiquity of platforms like Tor, making it ever easier for attackers to hide their traces and use commands through hidden servers to control the malware regarding how it attacks.
Who is behind all this?
As of now, Dragos claims that the malware is more than likely to be associated with the hacking group called Sandworm. This is because the same group had been identified perpetrating another attack back in 2014.In this attack, the targets were the Ukrainian and Polish governments along with European industries and the tool used to launch the attack was discovered to be BlackEnergy. In the 2015 attack, it was found that a more enhanced version, BlackEnery3 was used to hack into the power supply network.
It is likely that the malware will evolve even further as the likes of it are already out there in the wild.
